Information
security policy elaboration with mind map
Information security policy
as a global set of documents and measures to regulate organization activities
and ensure itsí safety. This set of documents has a complicated structure and
intercommunications between documents but it should be integral and actual at
every time line. Mind maps should be used to manage this complication. And Mind
Pad gives an opportunity to specify your map.
Information security policy
structure
First of all, you should know that there are many
different approaches to create ISP. We will consider the most global variant
when ISP describes all of organization activity aspects connected with
providing information security.
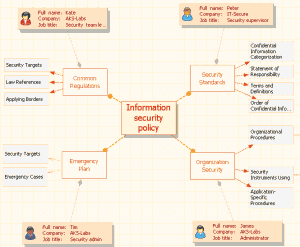
Our ISP will consist of 4 main parts: Common Regulations,
Security Standards, Organization Security and Emergency Plan.
Common Regulations devoted to defining such things as
Security Targets, Law References, Applying Borders and ISP structure.
Security Standards define Confidential Information
Categorization, Statement of
Responsibility, Terms and Definitions, Order of Confidential Information
Using and so on.
Organization Security is the main part and consist of 3
big and complicated chapters: Application-Specific Procedures, Organizational
Procedures and Security Instruments Using.
Emergency Plan consist of emergency situations defining,
priority placing, prior measures, emergency arrangements and recovery plan.
All documents in ISP have an addressing property. Some
docs are common for everyone, some should be
Information security policy
mind map
To get the best result you should use Mind Pad enhancement. In our ISP structure we
have common documents, which should be available for all, for-user documents
and administer documents. Users donít have access to administer documents.
Another division of documents is regulations (with such properties as
goal, access, borders and subject), standards (application area, access) and
instructions (access, subject), and ISP PART (part name and description). So,
we should create 4 new objects in Model Editor. Model Editor allows to create
class of frame objects with new properties. In simpler words it means that you
can add more properties to standard frames and use new frames on your
work-space.
So, we will have such new frames:
∑
regulation
∑
standard
∑
instruction
∑
ISP PART
For regulations we will specify
such category property values as application-specific procedure, organizational
procedure and security instruments using.
For access property we will
specify such values as: common, user and administrator.
Now we can create a mind map of
ISP in Mind Pad. Central topic is default frame called ISP. Subtopics are ISP
PARTS linked to ISP with names: Common Regulations, Security Standards,
Organization Security and Emergency Plan. Each ISP PART connected with its
regulations and standards and regulations are connected with instructions.
Access property specified for each frame. That is the main scheme of ISP mind
map.
As a tall structure it will
looks like the map designed in Mind Pad (click
to see the picture).
Of course, it is just an example, and you should
elaborate this model according to your organization specific.
Information security policy
support
To support ISP and keep it in an actual state we can link
frames with concrete document source, for example in Microsoft Word. So, now we
have an ISP specific workspace, we can see the whole structure of document set,
we know all access rights to each document and we can get each document
directly from the map using hyperlinks.
Such approach is very comfortable, because ISP may
consist of about 100 different documents and IT security specialist must keep
all this with its complicity and interconnections in his mind. For example,
Organization Security-> Organizational Procedures branch may have such
subtopics as Software Installation Order, Physical Access Order, Devices and Equipment Using Order, Access
Regulation and so on.
Mind Pad provides all needed instruments and opportunities
to create complete information security policy workspace. You also can use
notes to mark documents, for example, to specify its stage of development.
Sample maps
|
|
Information Security
Policy This is a
sample of security policy map created in Mind Pad. Download Security
Policy [11 KB] |
Map as a text
We have
generated a report for this map using Mind Pad. Here is the result:
|
1. |
Information security policy |
||||||
|
1.1. |
Common Regulations |
||||||
|
1.1.1. |
Security Targets |
||||||
|
1.1.2. |
Law References |
||||||
|
1.1.3. |
Applying Borders |
||||||
|
1.1.4. |
Kate |
||||||
|
|
|
||||||
|
1.2. |
Security Standards |
||||||
|
1.2.1. |
Confidential Information Categorization |
||||||
|
1.2.2. |
Statement of Responsibility |
||||||
|
1.2.3. |
Terms and Definitions |
||||||
|
1.2.4. |
Order of Confidential Information Using |
||||||
|
1.2.5. |
Peter |
||||||
|
|
|
||||||
|
1.3. |
Organization Security |
||||||
|
1.3.1. |
Organizational Procedures |
||||||
|
1.3.1.1. |
Software Installation Order |
||||||
|
1.3.1.1.1. |
Instruction (administrator) - Software Installation |
||||||
|
1.3.1.1.2. |
Instruction (user) - Software Using Rules |
||||||
|
1.3.2. |
Security Instruments Using |
||||||
|
1.3.2.1. |
Viruses Protection Order |
||||||
|
1.3.2.1.1. |
Organization of virus protection system |
||||||
|
1.3.2.1.2. |
Antivirus Software Using |
||||||
|
1.3.3. |
Application-Specific Procedures |
||||||
|
1.3.4. |
James |
||||||
|
|
|
||||||
|
1.4. |
Emergency Plan |
||||||
|
1.4.1. |
Security Targets |
||||||
|
1.4.2. |
Emergency Cases |
||||||
|
1.4.3. |
Tim |
||||||
|
|
|